Attack event details – H3C Technologies H3C SecCenter UTM Manager User Manual
Page 154
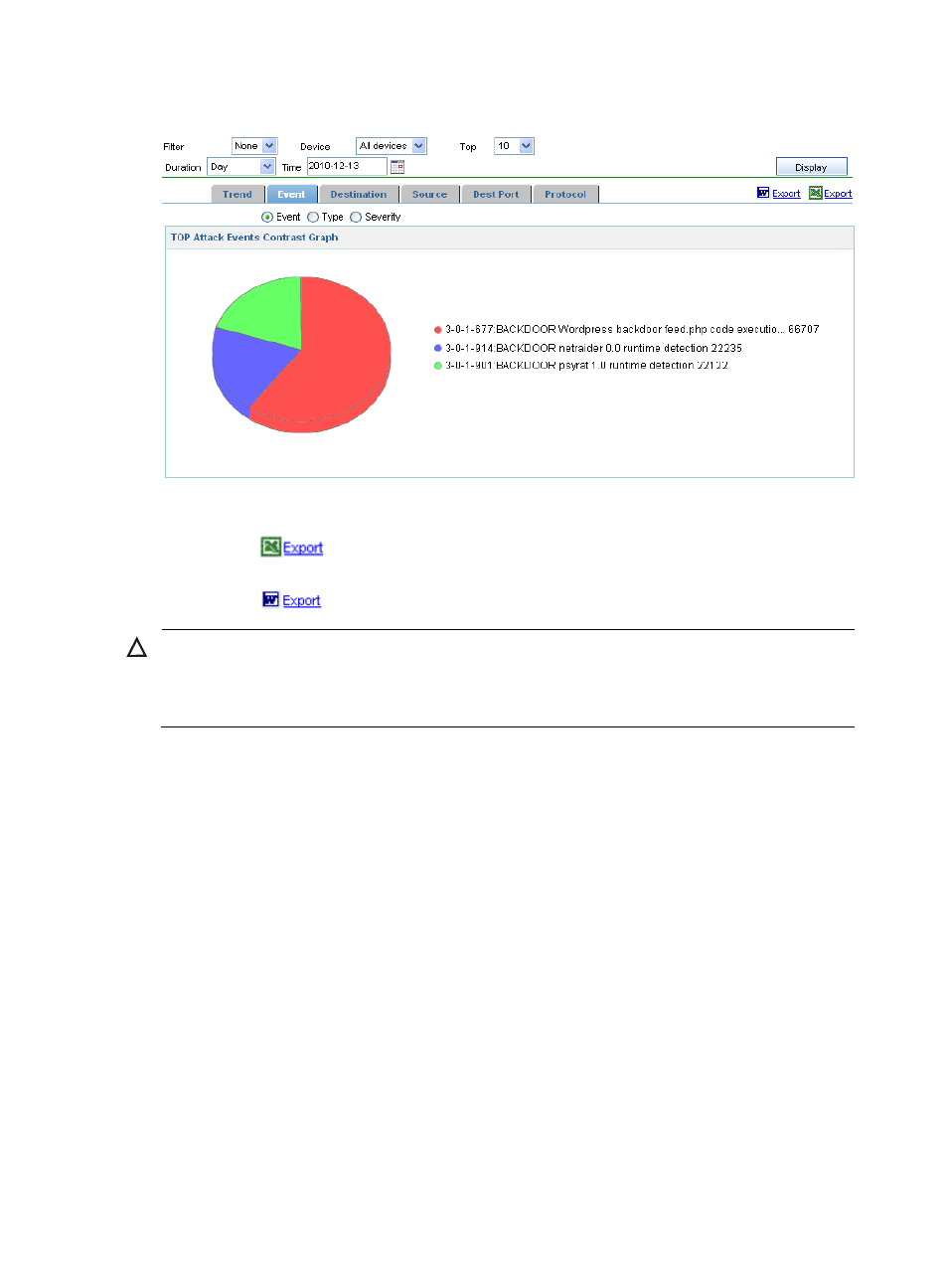
146
Figure 138 Top attack/virus events analysis
On the page, you can perform the following operations:
•
Click the
link to export all the analysis reports that the event analysis function provides to
an Excel file.
•
Click the
link to export the reports to a Word file.
CAUTION:
Logs are aggregated at 3 o’clock in the morning every day. When you query event information of the
current month, the system displays only the data collected from the first day of the month to the day before
the current day.
Attack event details
The UTM Manager provides the powerful query function, which helps you quickly find the desired
security event information from history data of months. The event information can be exported to an
HTML, Word, or Excel file.
From the navigation tree of the IPS management component, select Attack Event Details under Event
Analysis to enter the attack event details page, as shown in
. This page allows you to query
attack events by event name, type, severity, source IP address, destination IP address, destination port,
and protocol to view the attack event details.
describes the attack event query options.
describes the fields of the attack event details.