Configuring intrusion detection – H3C Technologies H3C SecCenter UTM Manager User Manual
Page 248
Advertising
240
NOTE:
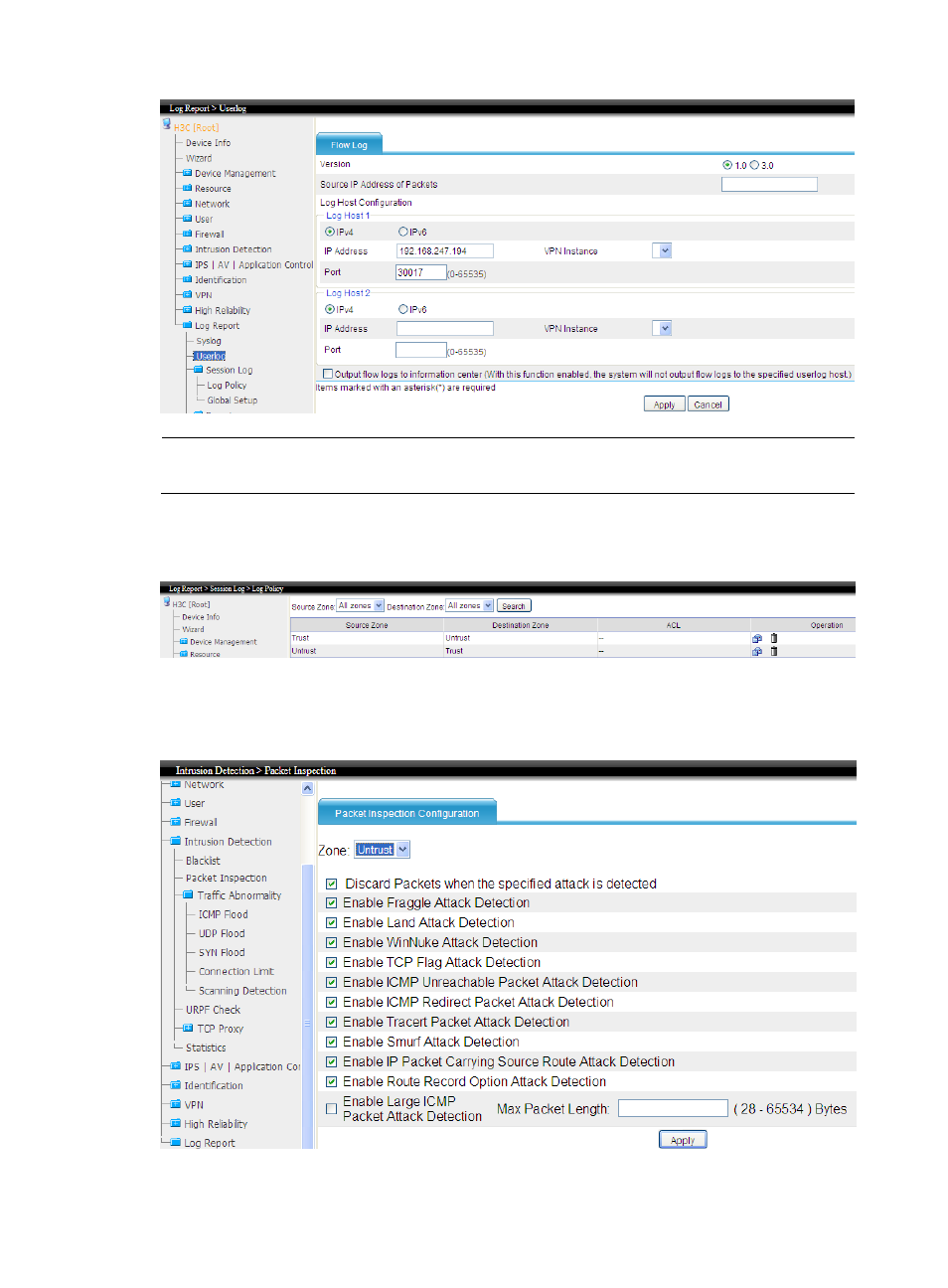
Flow logs refer to session logs only. To get flow logs, you must configure session logging as shown below.
3.
Configure a session logging policy
Select Log Report > Session Log > Log Policy from the navigation tree, and click Add to create two
policies as shown below.
Configuring intrusion detection
Select Intrusion Detection from the navigation tree, enable packet inspection, enable scanning detections,
blacklist and URPF check.
Advertising