Configuring attack protection policies, Configuration guide – H3C Technologies H3C SecCenter UTM Manager User Manual
Page 166
158
Configuring attack protection policies
Attack protection policies enable devices to filter attacks such as backdoor program, spyware, DoS
attacks, and DDoS attacks. On the attack protection policies management page, you can add, modify,
copy, and delete a user-defined attack protection policy.
NOTE:
attack_policy is the default attack protection policy. It cannot be modified or deleted.
Configuration guide
From the navigation tree of the IPS management component, select Attack Protection Policies under
Policy Management to enter the attack protection policies management page, as shown in
describes the attack policy management functions.
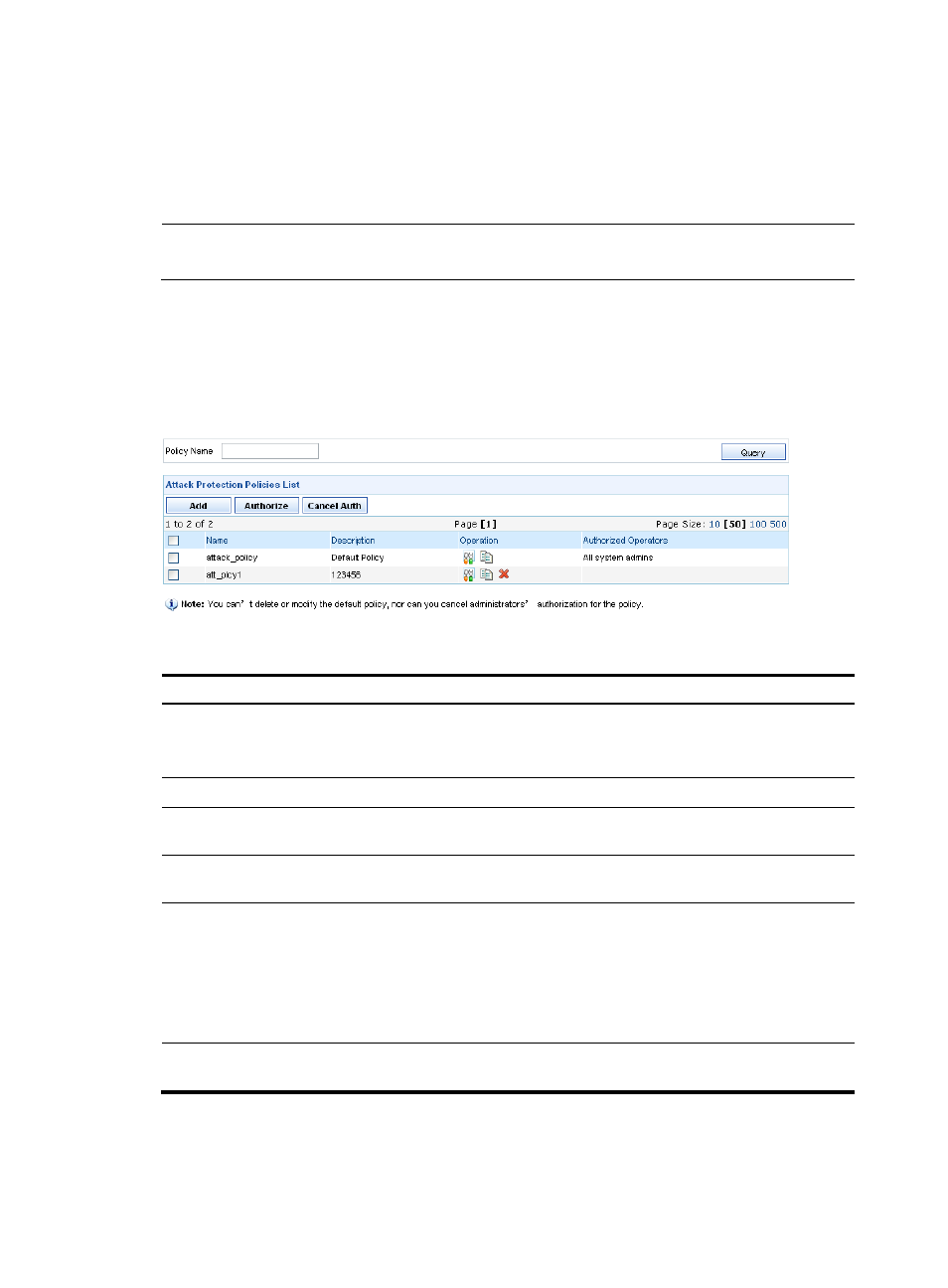
Figure 149 Attack protection policies management page
Table 135 Attack policy management functions
Function Description
Querying policies
Allows you to query policies by policy name.
Type a policy name keyword and click Query. The system will display all
attack protection policies whose names contain the keyword.
Attack protection policies list
Allows you to view all attack protection policies.
Adding an attack protection
policy
Allows you to add a new attack protection policy.
Deleting attack protection
policies
Allows you to delete attack protection policies.
Authorizing operators
Authorizes specific operators to manage the attack protection policies.
Follow these steps:
1.
Select the check boxes before the policies that you want to permit
operators to manage.
2.
Click Authorize.
3.
Select the operators, and click Apply.
Canceling authorization
Removes operators from the authorized operators of the task. The operation
procedure is similar to operator authorization procedure.