Security policy management, Managing security zones, Configuration guide – H3C Technologies H3C SecCenter UTM Manager User Manual
Page 214
206
Figure 200 Other log auditing
Security policy management
This function allows you to configure security policies for the firewall devices, so that the devices can
automatically identify and filter network traffic that travel through the devices. More specifically, this
function allows you to configure a series of rules to match packets between a source security zone and
a destination security zone, and permit or drop the matched packets.
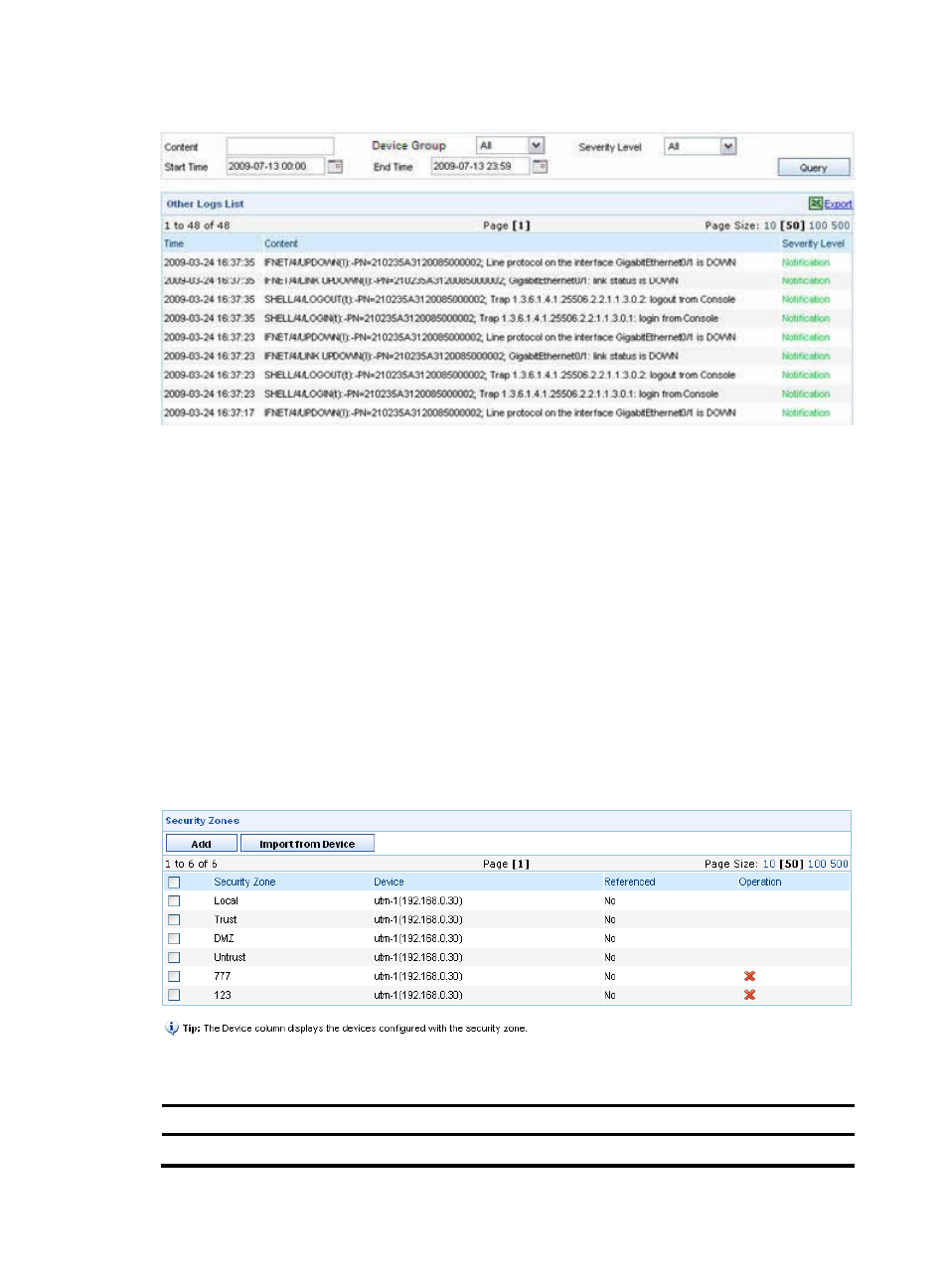
Managing security zones
Configuration guide
From the navigation tree of the firewall management component, select Security Zones under Security
Policy Management to enter the security zone management page, as shown in
describes the security zone management functions available on the page.
Figure 201 Security zone management page
Table 179 Security zone management functions
Function Description
Allows you to view the detailed information of all security zones.