Attack protection configuration examples, Network requirements, N in – H3C Technologies H3C MSR 50 User Manual
Page 194: Figure 175
Advertising
173
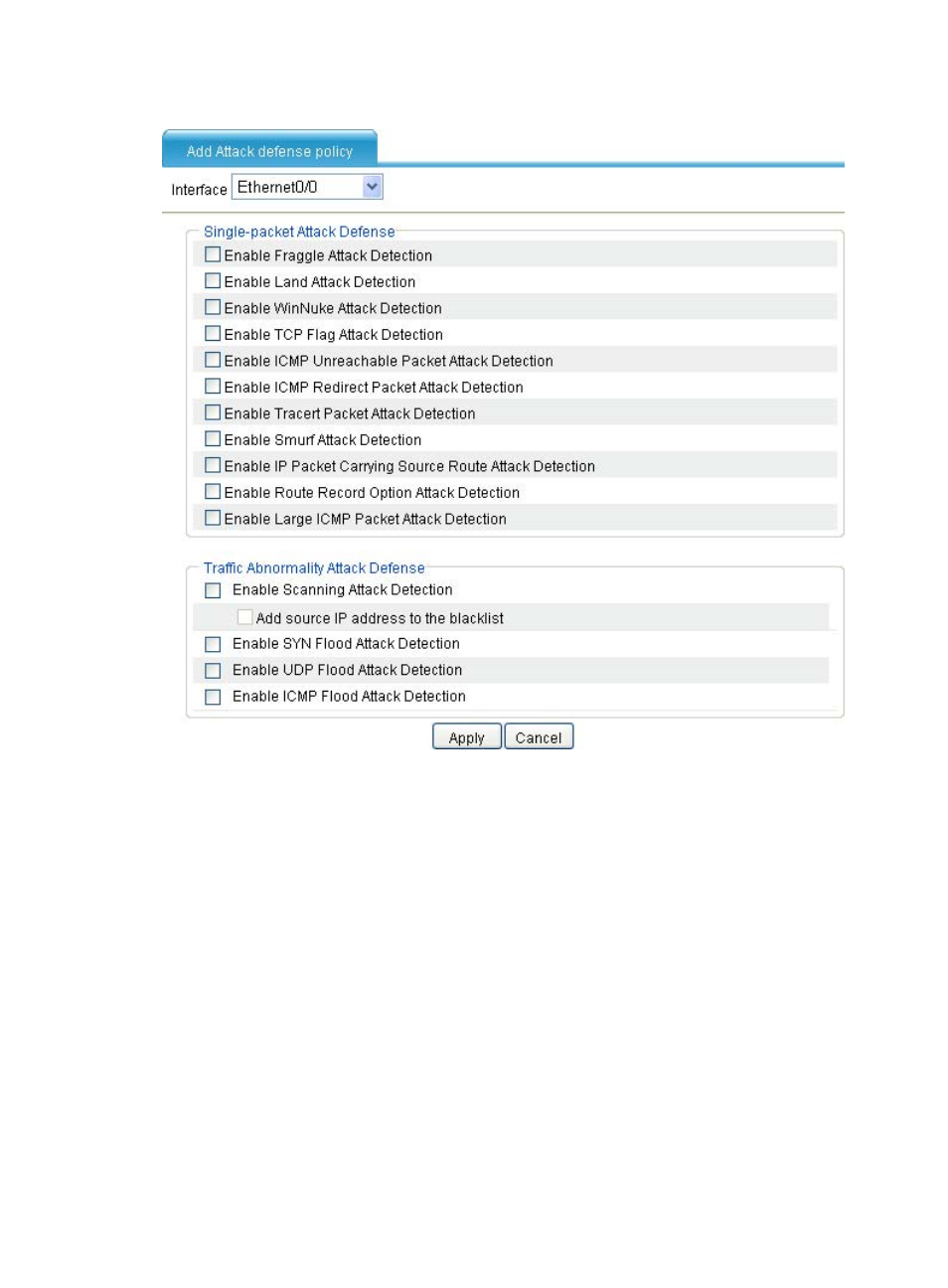
Figure 175 Add an intrusion detection policy
Attack protection configuration examples
Attack protection configuration example for MSR 900/20-1X
Network requirements
As shown in
, internal users Host A, Host B, and Host C access the Internet through Router. The
network security requirements are as follows:
•
Router always drops packets from Host D, an attacker.
•
Router denies packets from Host C for 50 minutes for temporary access control of Host C.
•
Router provides scanning attack protection and automatically adds detected attackers to the
blacklist.
•
Router provides Land attack protection and Smurf attack protection.
Advertising
This manual is related to the following products: