Configuring detection rule lists – H3C Technologies H3C WX3000E Series Wireless Switches User Manual
Page 491
Advertising
475
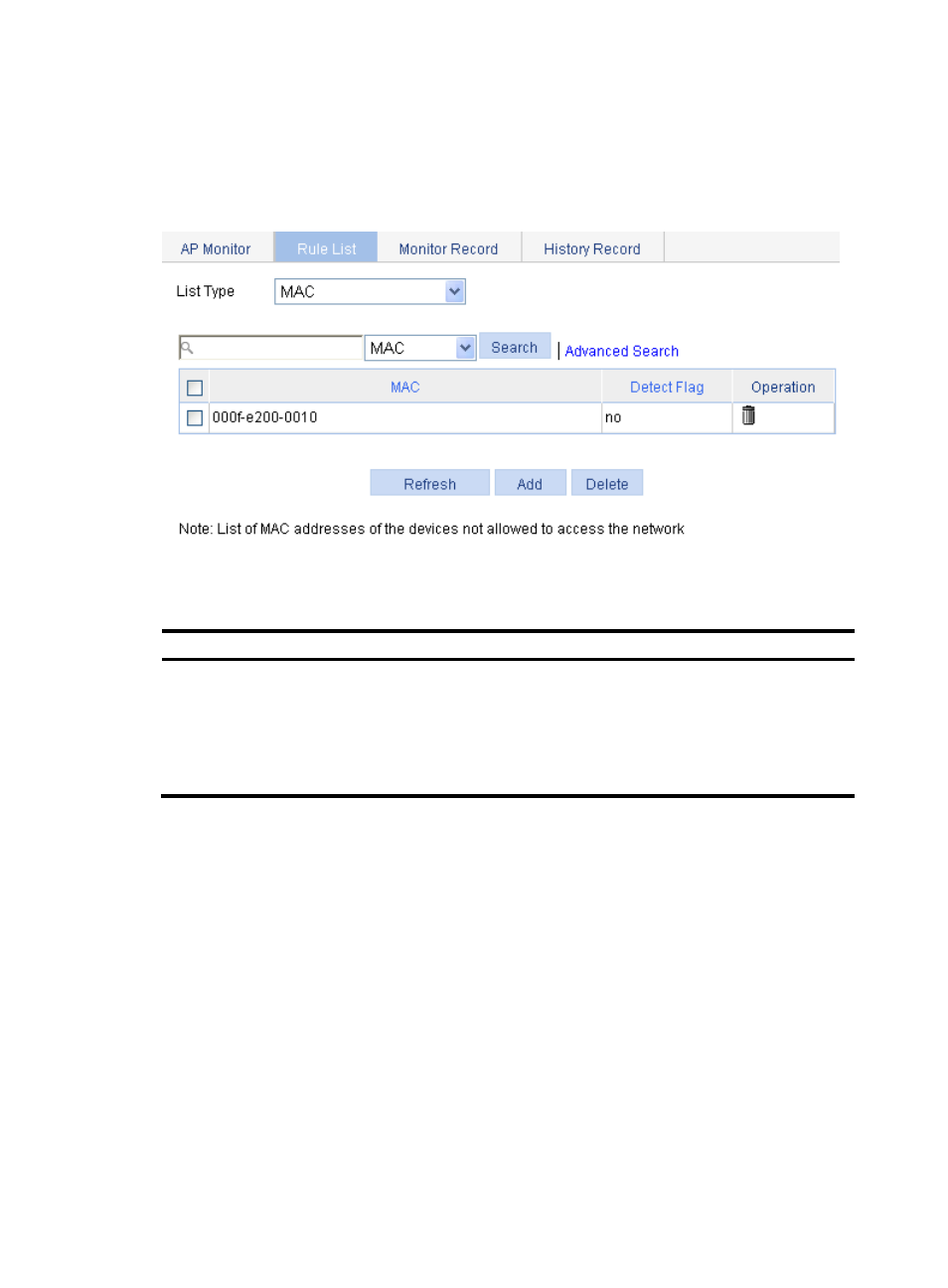
Configuring detection rule lists
1.
Select Security > Rogue Detection from the navigation tree.
2.
Click the Rule List tab to enter detection rule list configuration page.
Figure 508 Rule list configuration
3.
Configure the rule list as described in
Table 153 Configuration items
Item Description
List Type
•
MAC—You can add MAC addresses to be permitted after selecting this option.
•
Wireless Service—You can add SSIDs to be permitted after selecting this
option.
•
Vendor—You can specify vendors to be permitted after selecting this option.
•
Attacker—You can add the MAC address of a device to configure the device as
a rogue.
4.
Select MAC from the list and click Add to enter the MAC address configuration page.
Advertising
This manual is related to the following products: