H3C Technologies H3C WX3000E Series Wireless Switches User Manual
Page 244
228
As a port-based access control protocol, 802.1X authenticates and controls accessing devices at
the port level. A device connected to an 802.1X-enabled port of a WLAN access control device
can access the resources on the WLAN only after passing authentication.
The administrators of access devices can select to use RADIUS or local authentication to cooperate
with 802.1X for authenticating users. For more information about remote/local 802.1X
authentication, see "802.1X configuration."
3.
MAC authentication
MAC authentication provides a way for authenticating users based on ports and MAC addresses.
You can configure permitted MAC address lists to filter MAC addresses of clients. However, the
efficiency will be reduced when the number of clients increases. Therefore, MAC authentication is
applicable to environments without high security requirements, for example, SOHO and small
offices.
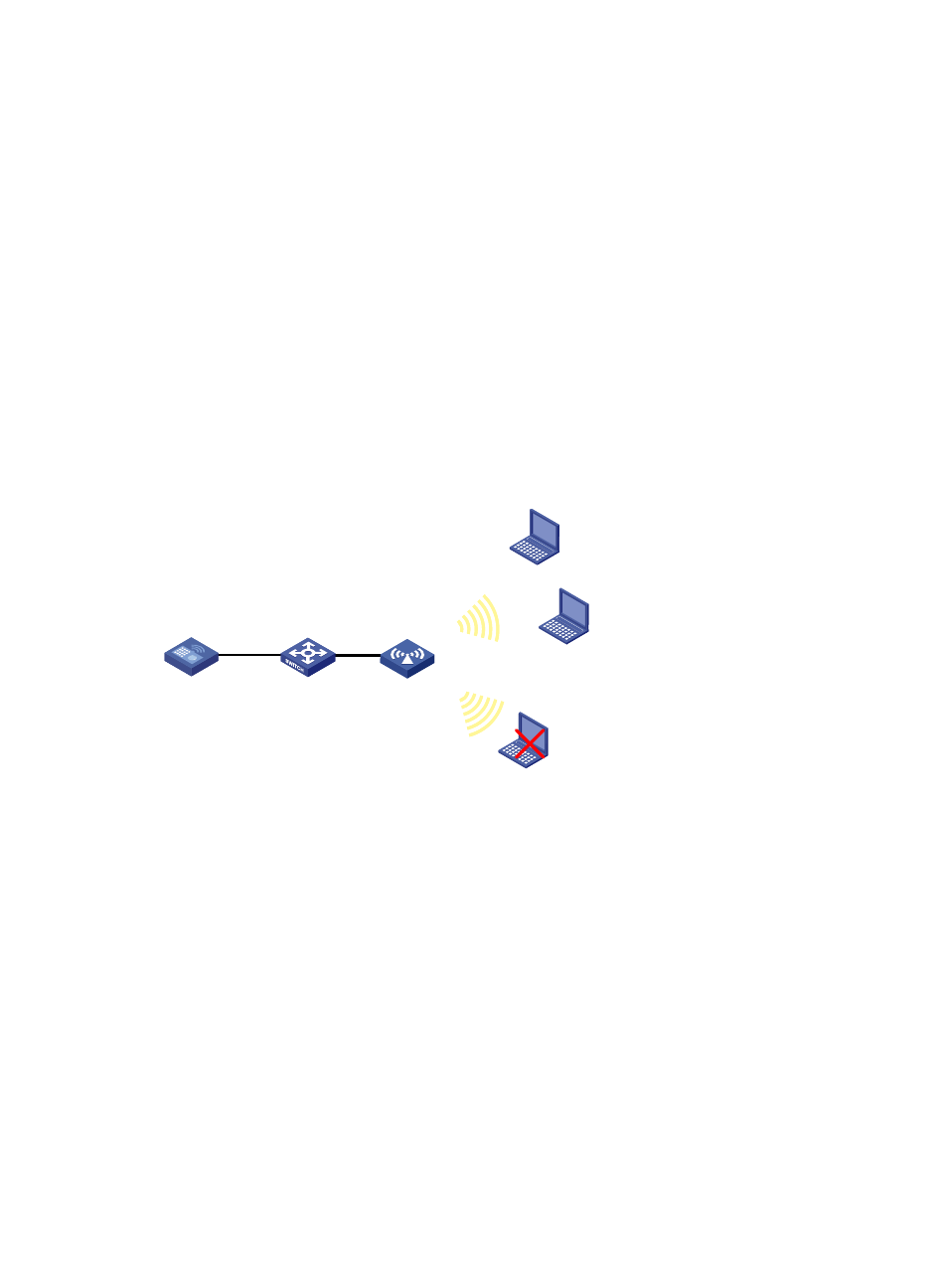
MAC authentication falls into two modes:
Local MAC authentication—When this authentication mode is adopted, you need to configure
a permitted MAC address list on the device. If the MAC address of a client is not in the list, its
access request will be denied.
Figure 217 Local MAC authentication
Remote MAC authentication—Remote Authentication Dial-In User Service (RADIUS) based
MAC authentication. If the device finds that the current client is an unknown client, it sends an
unsolicited authentication request to the RADIUS server. After the client passes the
authentication, the client can access the WLAN network and the corresponding authorized
information.
AC
L2 switch
AP
Client: 0009-5bcf-cce3
Permitted MAC
address list:
0009-5bcf-cce3
0011-9548-4007
000f-e200-00a2
Client: 0011-9548-4007
Client: 001a-9228-2d3e