Wlan security configuration example, Rogue detection configuration example, Network requirements – H3C Technologies H3C WX6000 Series Access Controllers User Manual
Page 503: Configuration procedure, Rogue detection configuration example -15, Table 42-10
42-15
Table 42-10 White list configuration items
Item
Description
MAC Address
Add a MAC address to the white list.
Select Current Connect
Client
If you select the check box, the table below lists the current existing clients. Select
the check boxes of the clients to add their MAC addresses to the white list.
WLAN Security Configuration Example
Rogue Detection Configuration Example
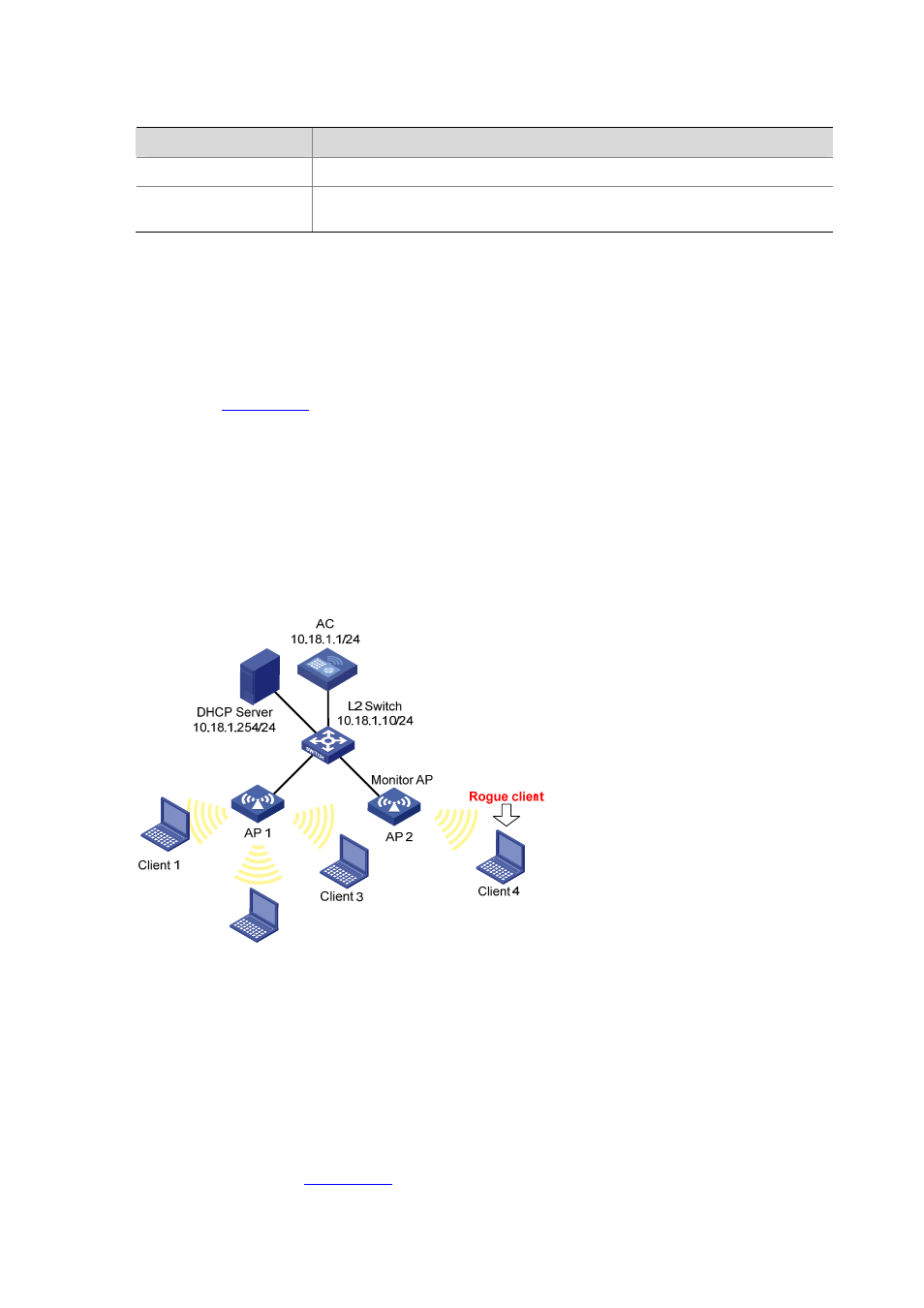
Network requirements
As shown in
, a monitor AP (AP 2 with serial ID 210235A29G007C000020) and AP 1 (serial
ID 210235A29G007C000022) are connected to an AC through a Layer 2 switch.
AP 1 operates in normal mode and provides WLAN data services only.
AP 2 operates in monitor mode, and scans all 802.11g frames in the WLAN.
Client 1 (MAC address 000f-e215-1515), Client 2 (MAC address 000f-e215-1530), and Client 3
(MAC address 000f-e213-1235) are connected to AP 1. They are configured as friends.
Client 4 (MAC address 000f-e220-405e) is connected to AP 2. It is configured as a rogue device.
Figure 42-21 WLAN security configuration
Configuration procedure
1) Configure AP 1 to operate in normal mode
In normal mode, AP 1 provides WLAN data services only. For how to configure WLAN services, refer to
Wireless Service Configuration.
2) Configure AP 2 to operate in monitor mode
# Add an AP.
Select AP > AP Setup in the navigation tree to enter the configuration page. Click Add to enter the AP
setup page as shown in