Westermo RedFox Series User Manual
Page 280
Westermo OS Management Guide
Version 4.17.0-0
INTERNET
PC
PC
Access controlled
ports
client
Authenticated
5
Switch
1
2
3
4
8
7
6
Server
Blocked
ports
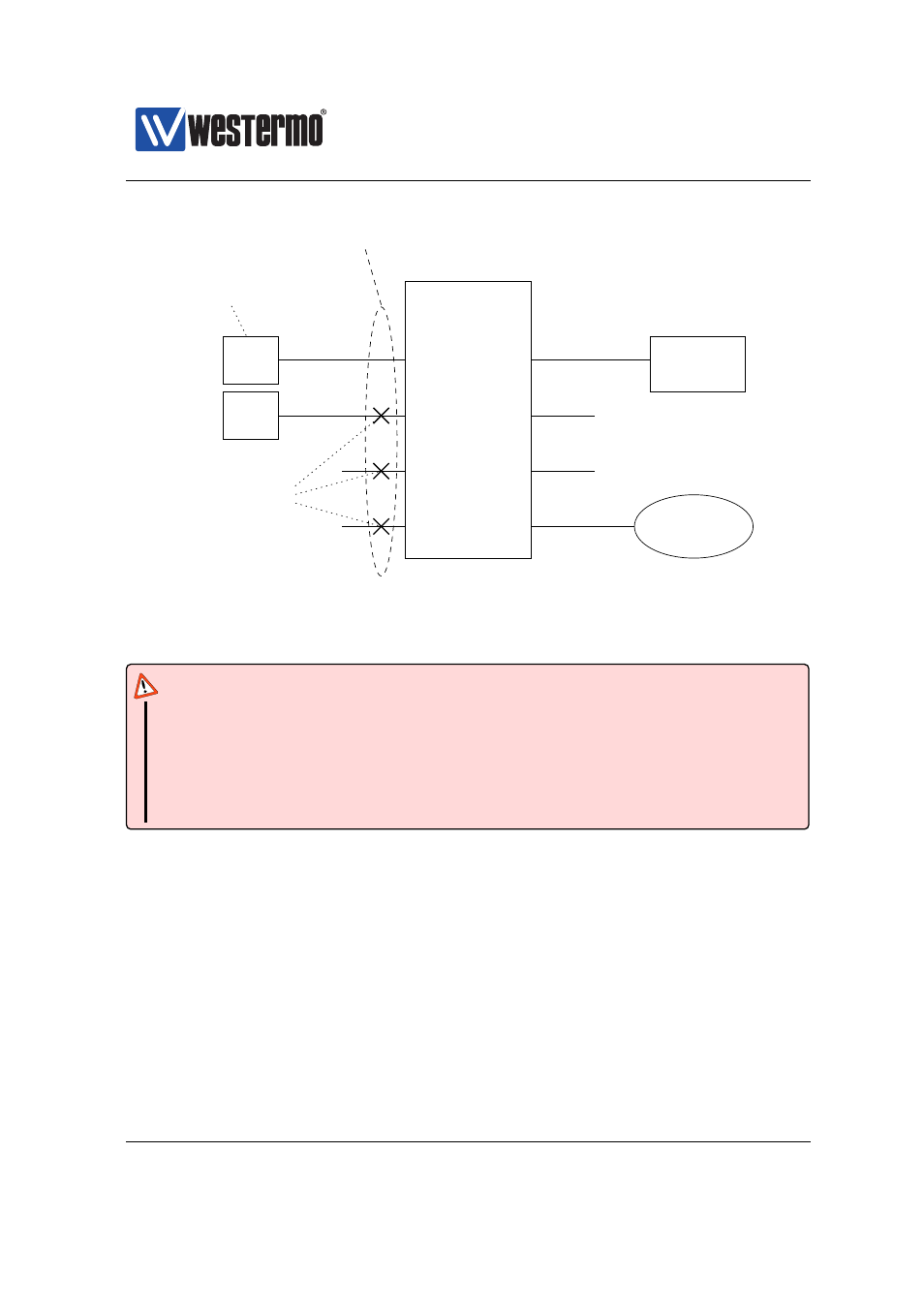
Figure 13.4: Port-based network access control
Port-based access control and VLAN trunk ports
As of WeOS v4.17.0, port-based access control is only working as expected
for access ports, i.e., ports only associated with a single VLAN (untagged).
VLAN trunk ports (ports associated tagged to one or more VLANs) should be
excluded from access control. Although it is possible to have access control
enabled on such ports, the behaviour is neither defined nor supported, and
may change in future WeOS releases.
In order to acquire access, the connected device needs to authenticate itself to
the switch. See
for a scenario. The PC on port 1 has authenticated it-
self, whereas the one on port 2 has not. The first PC is able to access the server
or the Internet connection on ports 6 and 8. The second PC or anything con-
nected to ports 3 or 4 will be blocked by the switch until they have authenticated
themselves.
The two authentication mechanisms available in WeOS for port-based network
access control are described further below: IEEE 802.1X in
and
MAC based authentication in
280
➞ 2015 Westermo Teleindustri AB