Application environment of trusted ports, Configuring trusted ports in a cascaded network, Application environment of trusted ports -25 – H3C Technologies H3C WX6000 Series Access Controllers User Manual
Page 220
26-25
Application Environment of Trusted Ports
Configuring a trusted port connected to a DHCP server
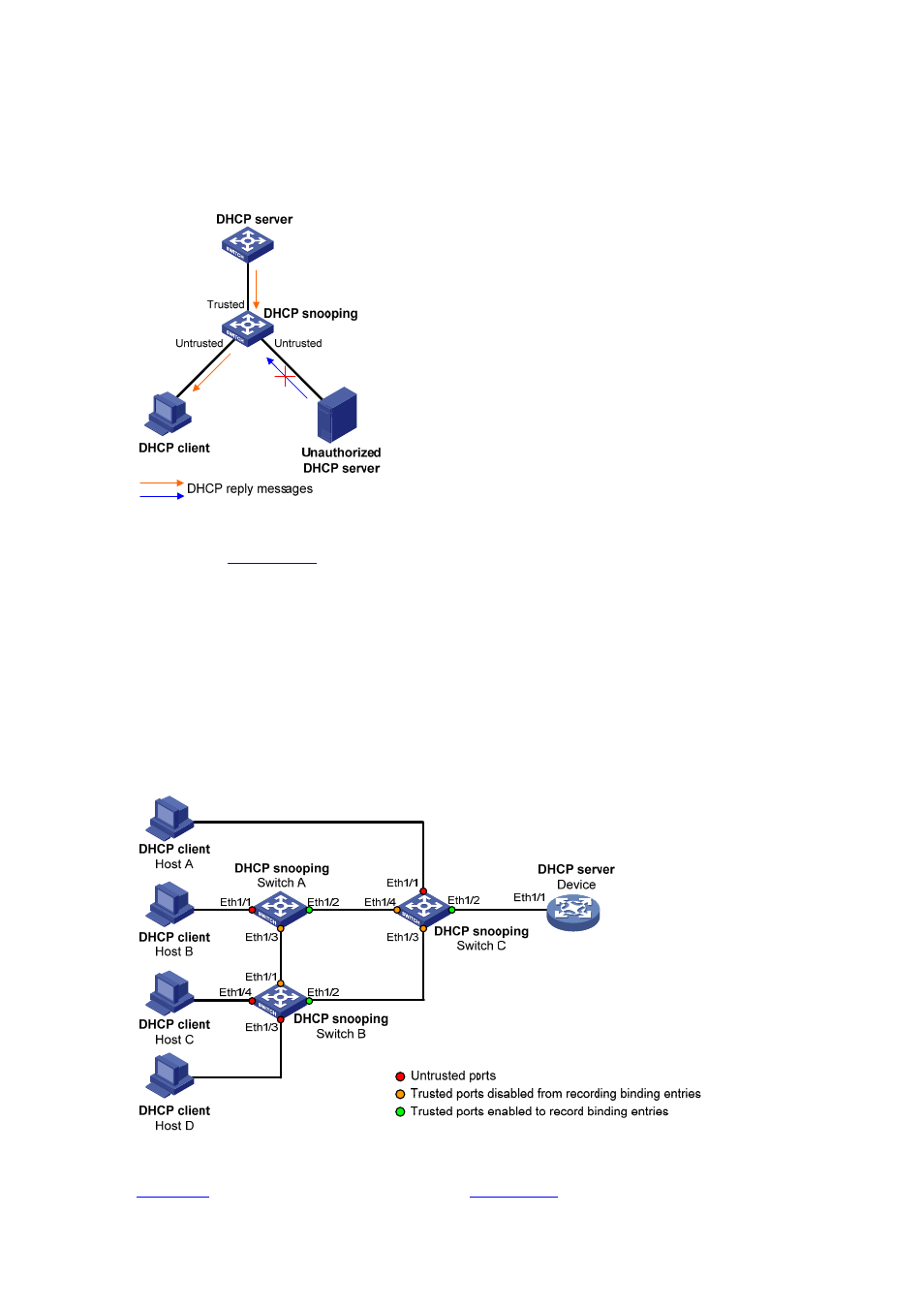
Figure 26-25 Configure trusted and untrusted ports
As shown in
, a DHCP snooping device’s port that is connected to an authorized DHCP
server should be configured as a trusted port to forward reply messages from the DHCP server, so that
the DHCP client can obtain an IP address from the authorized DHCP server.
Configuring trusted ports in a cascaded network
In a cascaded network involving multiple DHCP snooping devices, the ports connected to other DHCP
snooping devices should be configured as trusted ports.
To save system resources, you can disable the trusted ports, which are indirectly connected to DHCP
clients, from recording clients’ IP-to-MAC bindings upon receiving DHCP requests.
Figure 26-26 Configure trusted ports in a cascaded network
describes roles of the ports shown in