Displaying monitor record, Table 42-4 – H3C Technologies H3C WX6000 Series Access Controllers User Manual
Page 498
42-10
Table 42-4 MAC address list configuration items
Item
Description
MAC
Type the permitted MAC address in the text box.
Select the existent
devices
If you select this button, the MAC address table displays MAC addresses of the
current devices. Select the MAC addresses to be permitted.
The operation to add other types of lists is similar to the add operation of a MAC address list, and thus
the description is omitted.
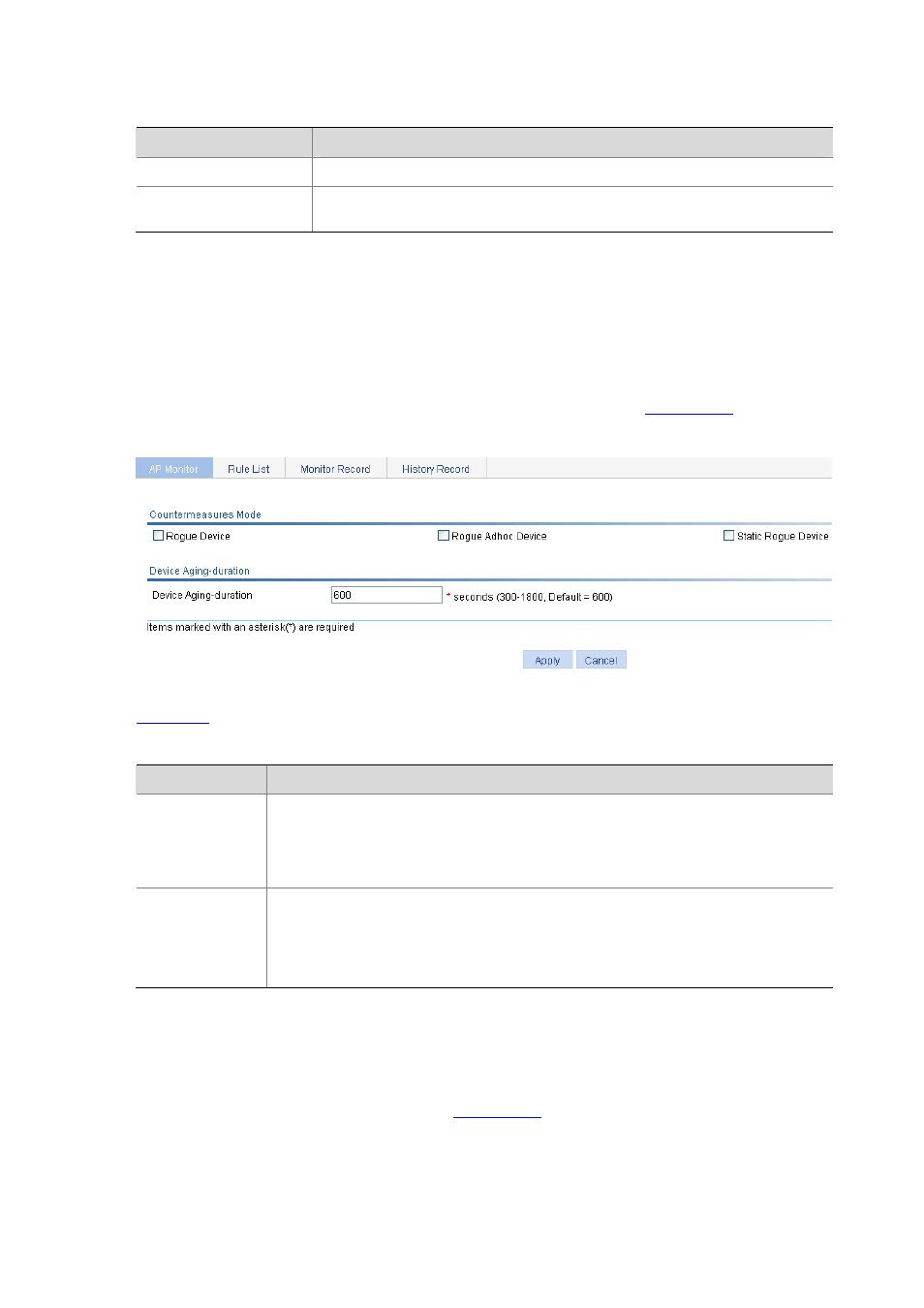
Enabling Countermeasures and Configuring Aging Time for Detected Rogue Devices
Select Security > Rogue Detection from the navigation tree, and then select the AP Monitor tab. On
the page, click Common Set to enter the configuration page, as shown in
.
Figure 42-12 Countermeasures configuration
describes the common configuration items.
Table 42-5 Common configuration items
Item
Description
Contermeasures
Mode
Rogue Device: Allows you to take countermeasures against rogue devices (including
illegal APs and illegal clients).
Rogue Adhoc Device: Allows you to take countermeasures against ad hoc devices.
Static Rogue Device: Allows you to take countermeasures against rogue devices
configured in the detection rule list.
Device
Aging-duration
Configure the aging time of entries in the device list.
Once a rogue device is detected, an entry for it is added to the monitor record and the
aging time starts. The aging time restarts if the device is detected again during the time.
When the aging time is reached, the entry is deleted from the monitor record and added to
the history record.
Displaying Monitor Record
Select Security > Rogue Detection from the navigation tree, and then select the Monitor Record tab
to enter the monitor record page, as shown in