Displaying history record, Displaying statistics information, Figure 42-15 – H3C Technologies H3C WX6000 Series Access Controllers User Manual
Page 500
42-12
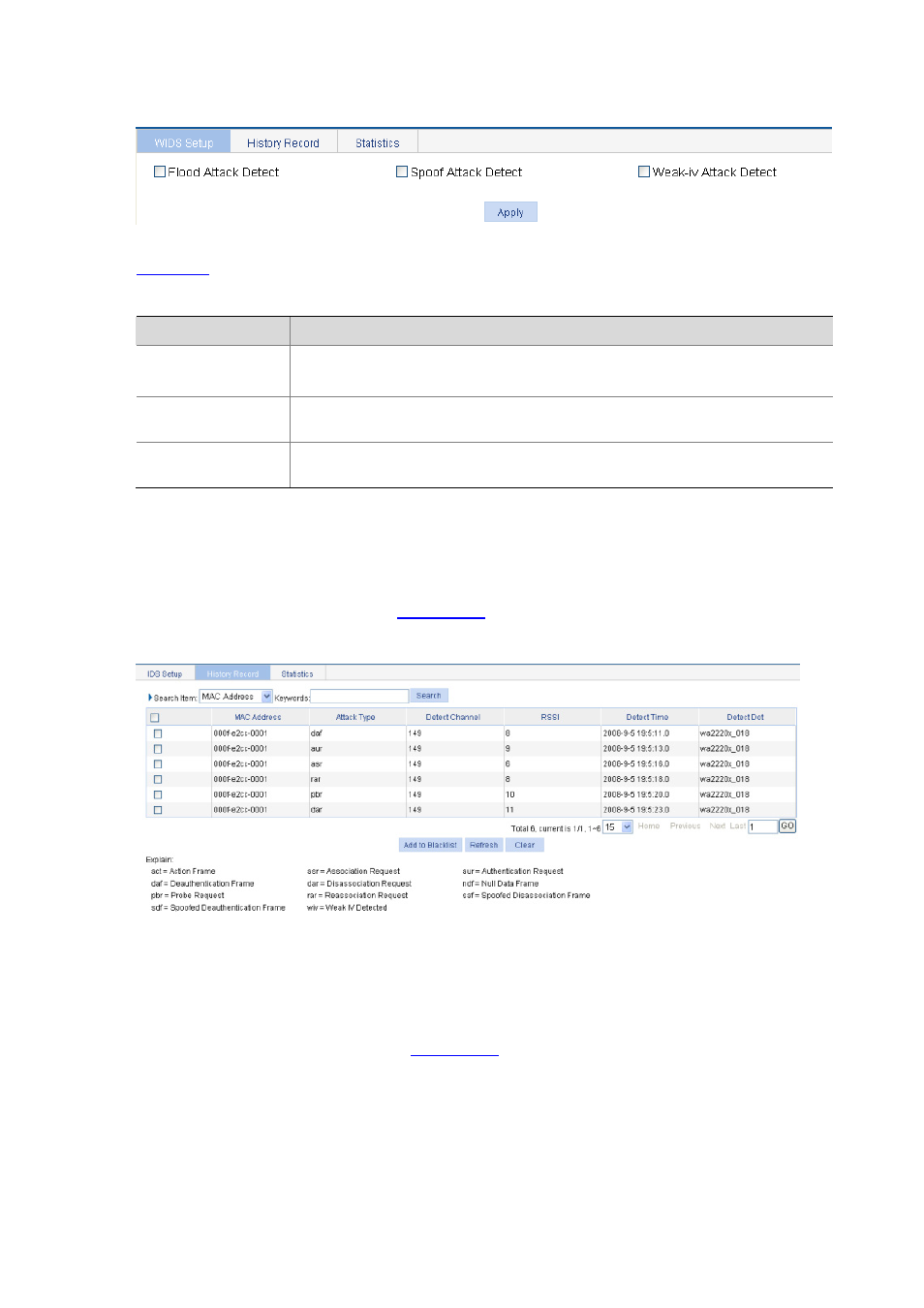
Figure 42-15 WIDS configuration
describes the WIDS configuration items.
Table 42-7 WIDS configuration items
Item
Description
Flood Attack Detect
If you select the check box, flood attack detection is enabled.
It is disabled by default.
Spoof Attack Detect
If you select the check box, spoofing attack detection is enabled. It is disabled by
default.
Weak-iv Attack Detect
If you select the check box, Weak IV attack detection is enabled. It is disabled by
default.
Displaying History Record
Select Security > WIDS from the navigation tree, and then select the History Record tab to enter the
history information page, as shown in
Figure 42-16 History information
Displaying Statistics Information
Select Security > WIDS from the navigation tree, and then select the Statistics tab to enter the
statistics information page, as shown in