Configuring detection rule lists – H3C Technologies H3C WX6000 Series Access Controllers User Manual
Page 497
42-9
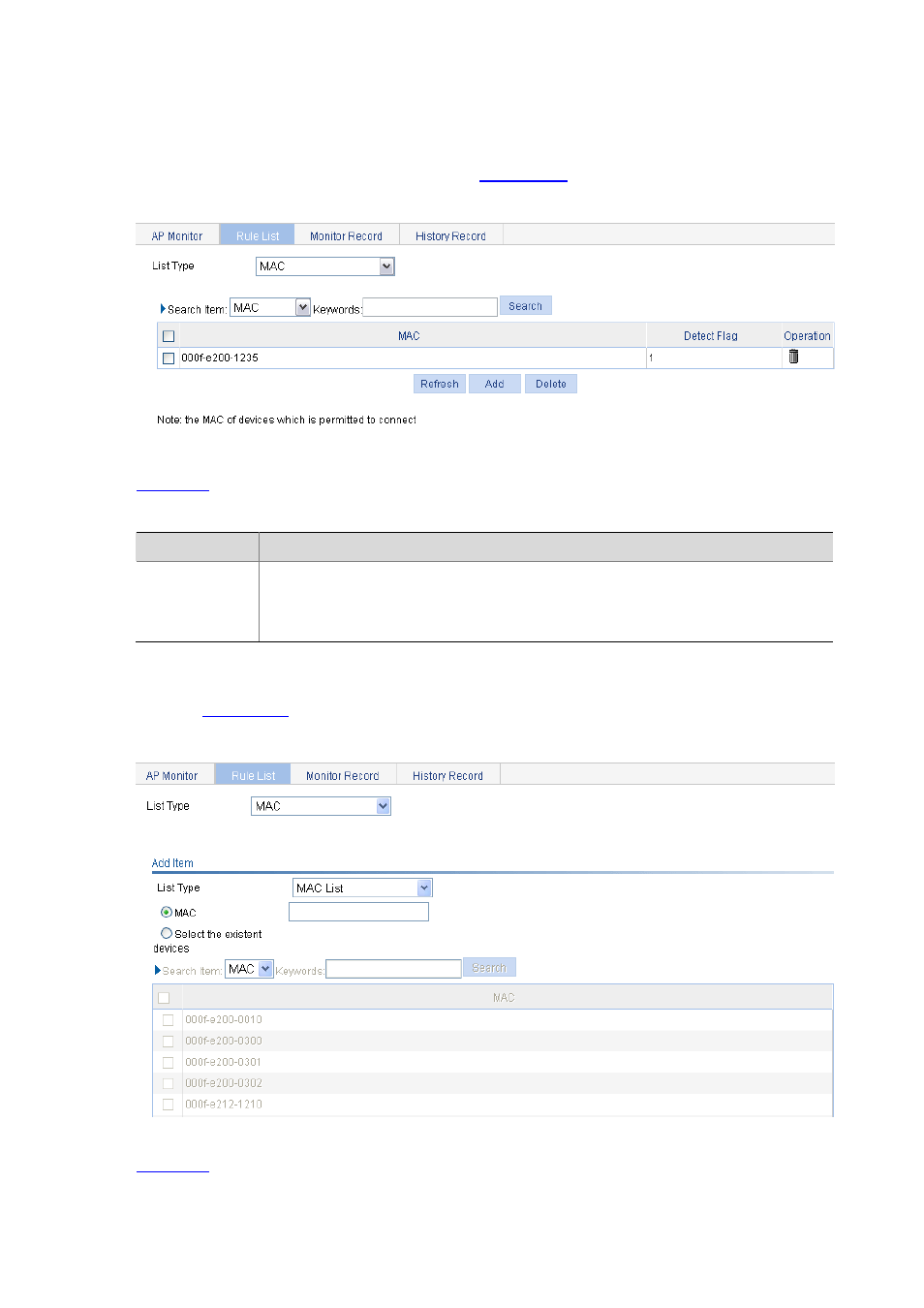
Configuring Detection Rule Lists
Select Security > Rogue Detection from the navigation tree, and then select the Rule List tab to enter
detection rule list configuration page, as shown in
.
Figure 42-10 Rule list configuration
describes the rule list configuration items.
Table 42-3 Rule list configuration items
Item
Description
List Type
MAC: You can add MAC addresses to be permitted after selecting this option.
Wireless Service: You can add SSIDs to be permitted after selecting this option.
Vendor: You can specify vendors to be permitted after selecting this option.
Attacker: You can add the MAC address of a device to configure the device as a rogue.
Select MAC from the drop-down list and click Add to enter the MAC address configuration page, as
shown in
.
Figure 42-11 MAC address list configuration page
describes configuration items for configuring MAC address list.