Boot-time defenses, Operating system defenses – Microsoft Surface Hub 2 SmCamera User Manual
Page 294
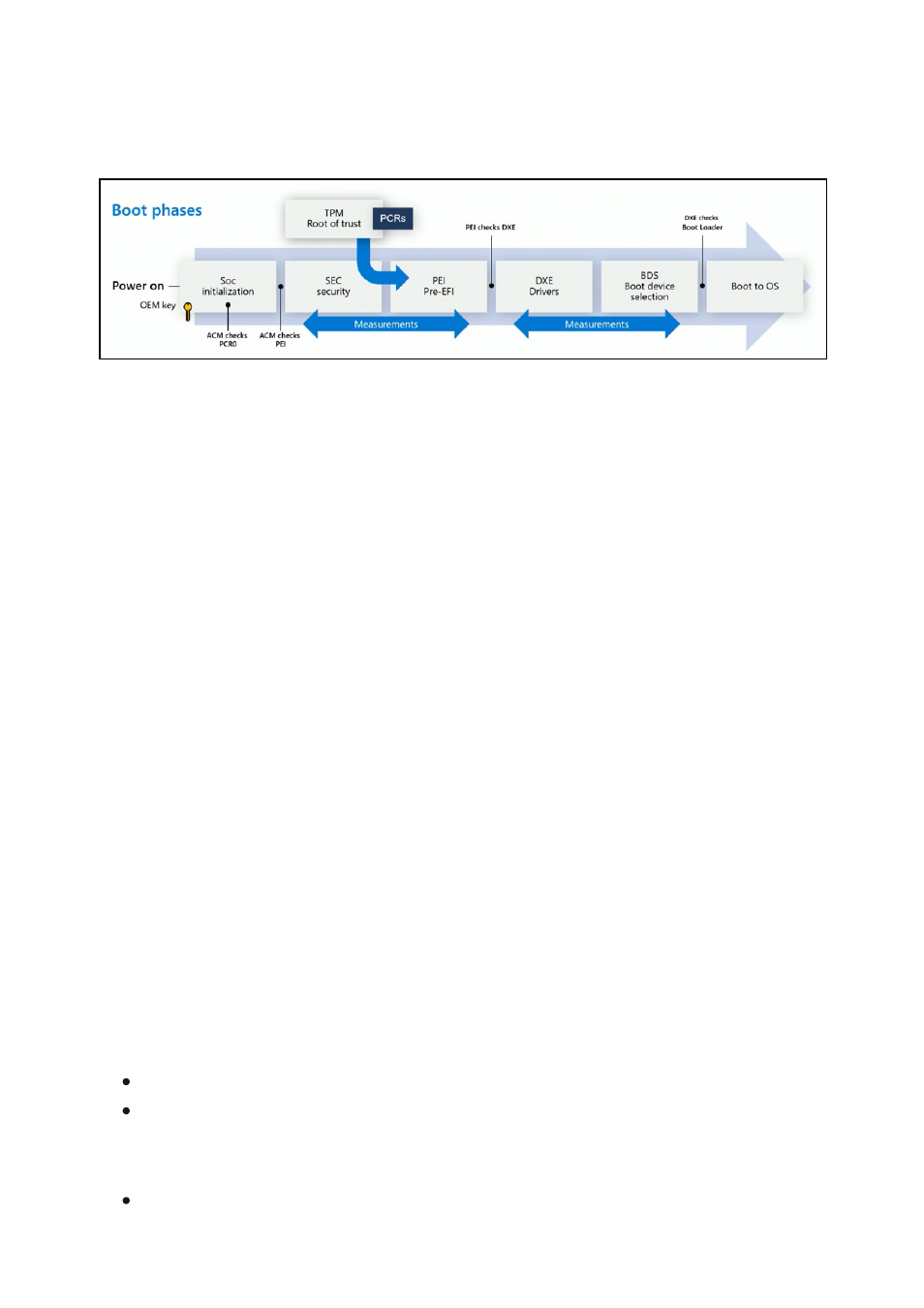
The SoC has a security processor that's separate from every other core. When you first
start Surface Hub, the security processor starts before anything else can be loaded.
Secure Boot is used to verify that the components of the boot process, including drivers
and the operating system, are validated against a database of valid and known
signatures. On Surface Hub, a platform-specific signature must first be validated before
the authorized Windows Team operating system can be loaded. This helps prevent
attacks from a cloned or modified system running malicious code hidden in what
Once the operating system is verified as originating from Microsoft and Surface Hub
successfully completes the boot process, the device scrutinizes the executable code. Our
approach to securing the operating system involves identifying the code signature of all
executables, allowing only those that pass our restrictions to be loaded into the runtime.
This code-signing method enables the operating system to verify the author and
confirm that code was not altered prior to running on the device.
Surface Hub uses a code signing feature known as User Mode Code Integrity (UMCI) in
Windows Application Control (formerly known as Device Guard). Policy settings are
configured to only allow apps that meet one of these requirements:
Universal Windows Platform (Microsoft Store) apps that are
Apps signed with the unique Microsoft Production Root Certification Authority
(CA), which can only be signed by Microsoft employees with authorized access to
those certificates.
Apps signed with the unique Surface Hub Production Root C.
Boot-time defenses
Secure Boot
Operating system defenses