Westermo RedFox Series User Manual
Page 805
Westermo OS Management Guide
Version 4.17.0-0
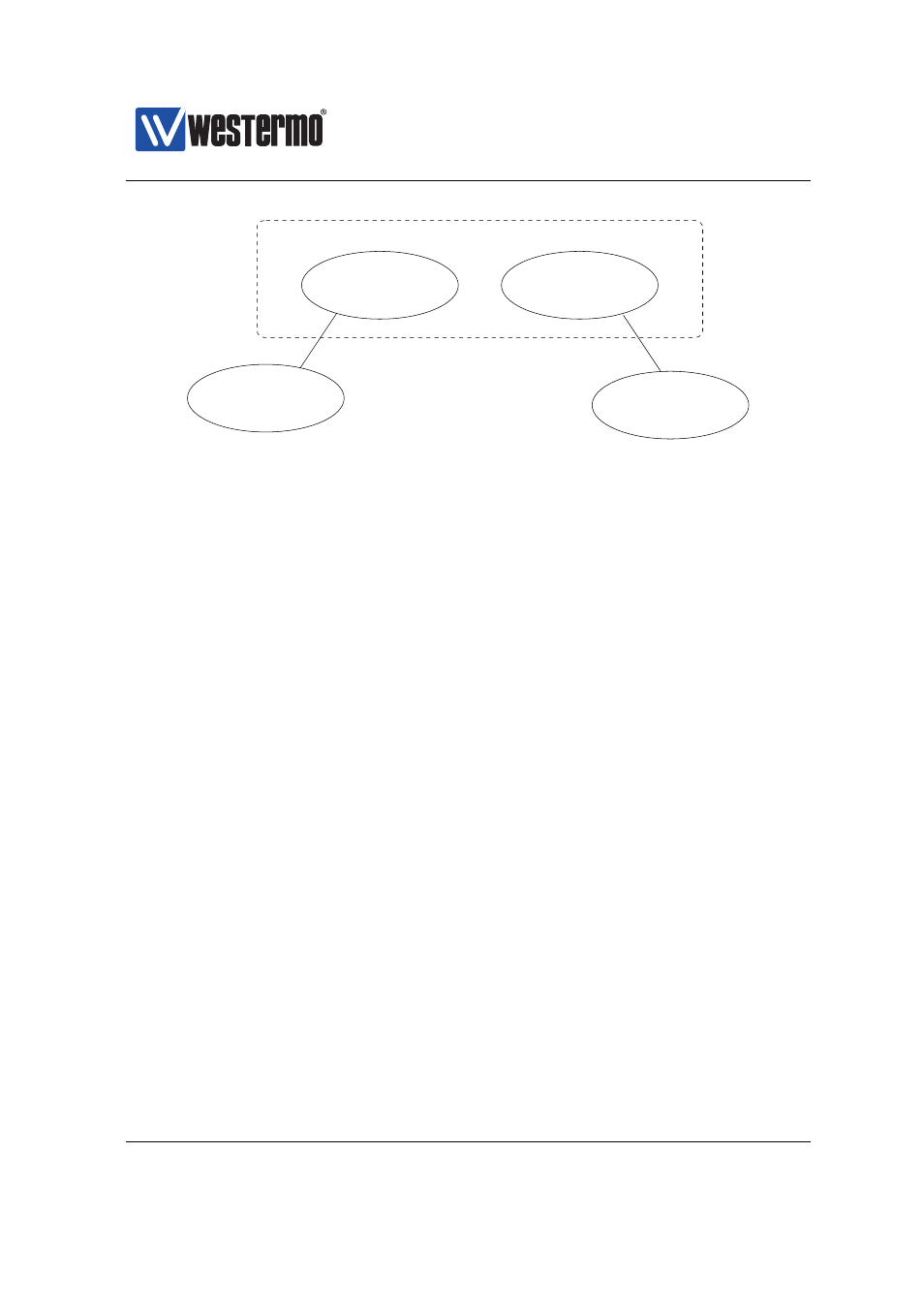
Alice
CA
A
CA
B
Bob
Trusted CAs
Figure 35.8: Alice and Bob have certificates issued by different CAs (e.g., their
respective company CA). In this PKI model, Alice uploads the certificate of her CA
(CA
A
), and Bob’s CA (CA
B
), and trusts any certificate issued by either of them CA.
In this user scenario, a VPN unit such as Alice will have to upload/import
❼ the certificate of her CA (CA
A
),
❼ the certificate of Bob’s CA (CA
B
),
❼ her own certificate (AliceCert), and
❼ the private key associated with her certificate.
Alice would typically upload/import her private key, her CA and own certificates
as a password protected PKCS#12 bundle, while Bob’s CA certificate could be
uploaded/imported as a PEM file. See
for more information on cer-
tificate management).
If we consider the sample setup in
, the certificates of Alice and Bob
would now be issued by different CAs. Below we see sample WeOS CLI syntax for
Alice’s and Bob’s VPN configuration, as well as some comments.
❼ Remote CA: The setting ”remote-ca dn ´’C=US, O=FOOBAR, CN=FoobarCA´’”
in Alice’s configuration restricts initiators to have certificates issued by the
”FoobarCA” (Bob’s CA). An alternative would be to use the setting ”remote-ca
any”, which would allow initiators with valid certificates issued by any CA
trusted by Alice.
Correspondingly, Bob is configured to only trust certificates issued by ”AcmeCA”
(Alice’s CA).
As of WeOS v4.17.0, the Remote CA setting is only configurable via the CLI,
➞ 2015 Westermo Teleindustri AB
805