Transparent mac authentication, Uam configuration – H3C Technologies H3C Intelligent Management Center User Manual
Page 63
45
Transparent MAC authentication
This transparent authentication method is based on MAC addresses. With this authentication method
enabled, UAM automatically authenticates an endpoint as soon as the endpoint is trying to connect to
the network.
To implement transparent MAC authentication, you must configure UAM and the access device.
UAM configuration
In addition to the
in
802.1X authentication and UAM local authentication
, you must
perform the following configurations:
•
Enable transparent MAC authentication in UAM. For more information, see "
•
Enable transparent MAC authentication for a specific endpoint device.
To enable transparent MAC authentication for a specific endpoint device, use the following methods:
•
Enable transparent MAC authentication in UAM with operator privilege.
This method applies to the endpoint devices whose MAC addresses UAM already obtains.
{
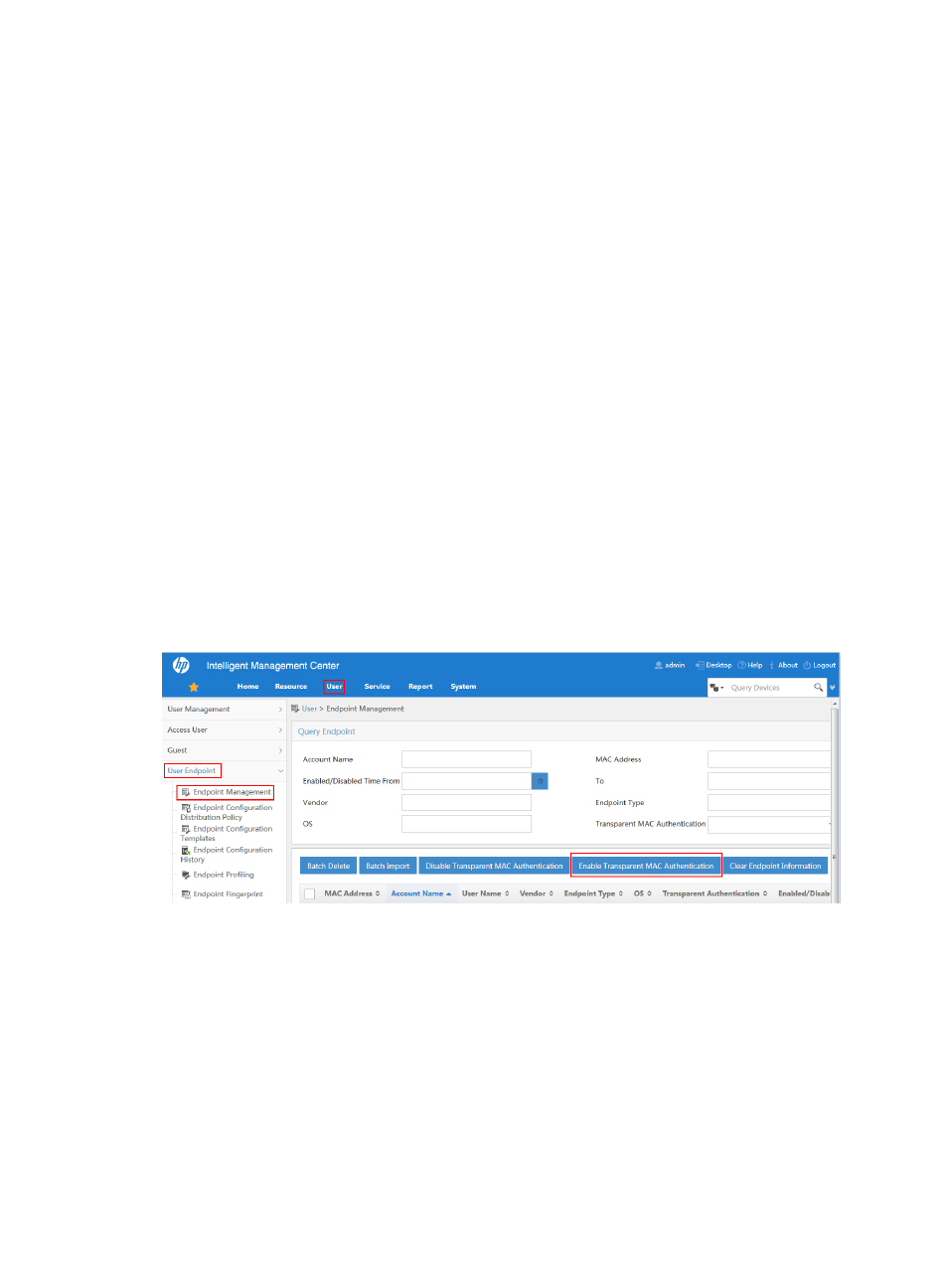
To access the endpoint device address list page, click the User and select User Endpoint >
Endpoint Management from the navigation tree.
{
Select target endpoint devices and click Enable Transparent Authentication.
Figure 35 Enabling transparent MAC authentication with operator privilege
•
Enable transparent MAC authentication in the user self-service center.
{
To access the Endpoint List page, select Endpoint Management > MAC Address Entry from the
navigation tree.
{
Select target MAC addresses and click Enable Transparent Authentication. If the target MAC
addresses are not in the list, you can first add them to the list. Each of the MAC addresses in the
list is bound with an access user.
The results for the operations of adding/deleting endpoint devices, and changing transparent
MAC authentication status on endpoint device are synchronized to the endpoint device
address list in UAM.