Security parameter dependencies, Table 130 – H3C Technologies H3C WX3000E Series Wireless Switches User Manual
Page 381
360
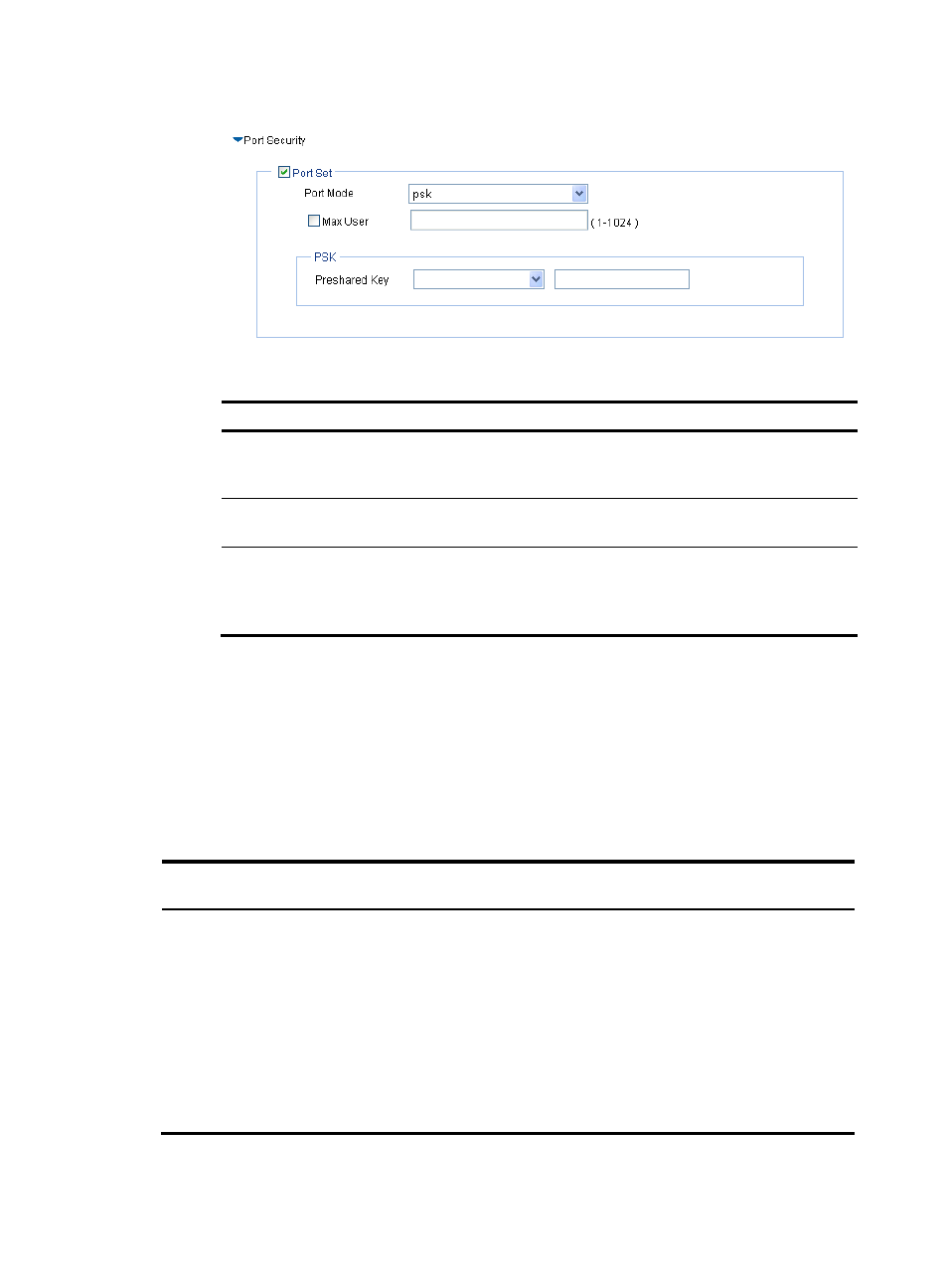
Figure 342 Configuring psk port security
Table 129 Configuration items
Item Description
Port Mode
psk: An access user must use the pre-shared key (PSK) that is pre-configured to
negotiate with the device. The access to the port is allowed only after the
negotiation succeeds.
Max User
Control the maximum number of users allowed to access the network through
the port.
Preshared Key
•
pass-phrase—Enter a PSK in the form of a character string. You must enter
a string that can be displayed and consists of 8 to 63 characters.
•
raw-key—Enter a PSK in the form of a hexadecimal number. You must enter
a valid 64-bit hexadecimal number.
c.
Configure userlogin-secure-ext:
Perform the configurations shown in
Configure userlogin-secure/userlogin-secure-ext
.
Security parameter dependencies
For a clear-type wireless service or crypto-type wireless service, the security parameter dependencies are
shown in
.
Table 130 Security parameter dependencies
Service
type
Authenticati
on mode
Encryption
type
Security IE
WEP
encryption/key ID Port mode
Clear Open-System
Unavailable Unavailable Unavailable
•
mac-authentication
•
mac-else-userlogin-secu
re
•
mac-else-userlogin-secu
re-ext
•
userlogin-secure
•
userlogin-secure-ext
•
userlogin-secure-or-mac
•
userlogin-secure-or-mac
-ext