Enabling countermeasures and configuring, Aging time for detected rogue devices – H3C Technologies H3C WX3000E Series Wireless Switches User Manual
Page 641
620
5.
Configure the MAC address list as described in
Table 196 Configuration items
Item Description
MAC
Enter the permitted MAC address in the box.
Select the existent
devices
If you select this option, the MAC address table displays MAC addresses of the
current devices. Select the MAC addresses to be permitted.
6.
Click Apply.
The operation to add other types of lists is similar to the add operation of a MAC address list, so the
description is omitted.
Enabling countermeasures and configuring aging time for
detected rogue devices
1.
Select Security > Rogue Detection from the navigation tree.
2.
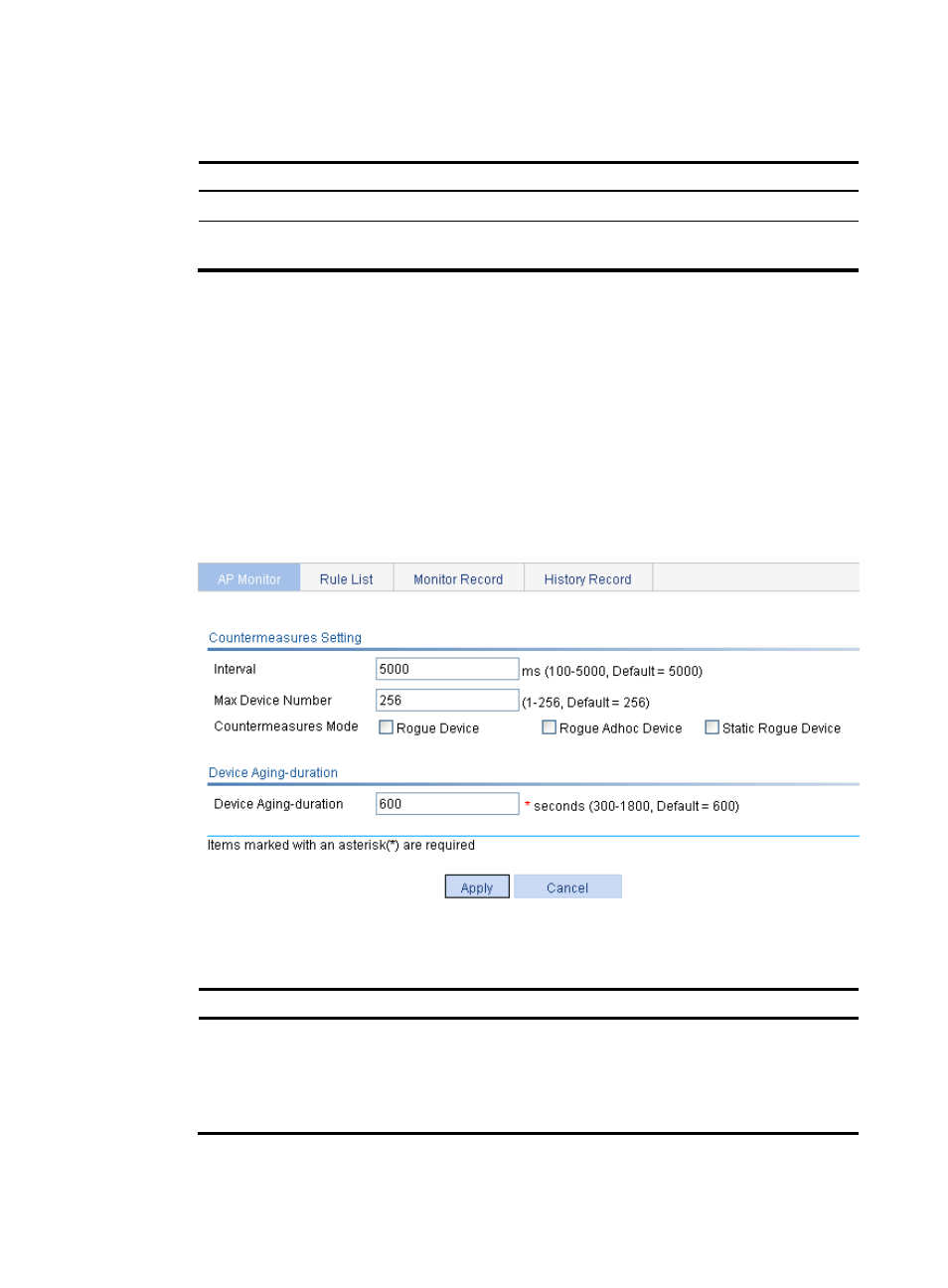
On the AP Monitor tab, click Common Set.
Figure 656 Common configuration
3.
Perform common configuration as described in
Table 197 Configuration items
Item Description
Countermeasures
Setting
Configure the AP to take countermeasures against rogue devices while
providing wireless services.
•
Interval—The interval at which the AP takes countermeasures.
•
Max Device Number—The maximum number of rogue devices that the AP
can take countermeasures against.