Configuring detection rule lists – H3C Technologies H3C WX3000E Series Wireless Switches User Manual
Page 640
Advertising
619
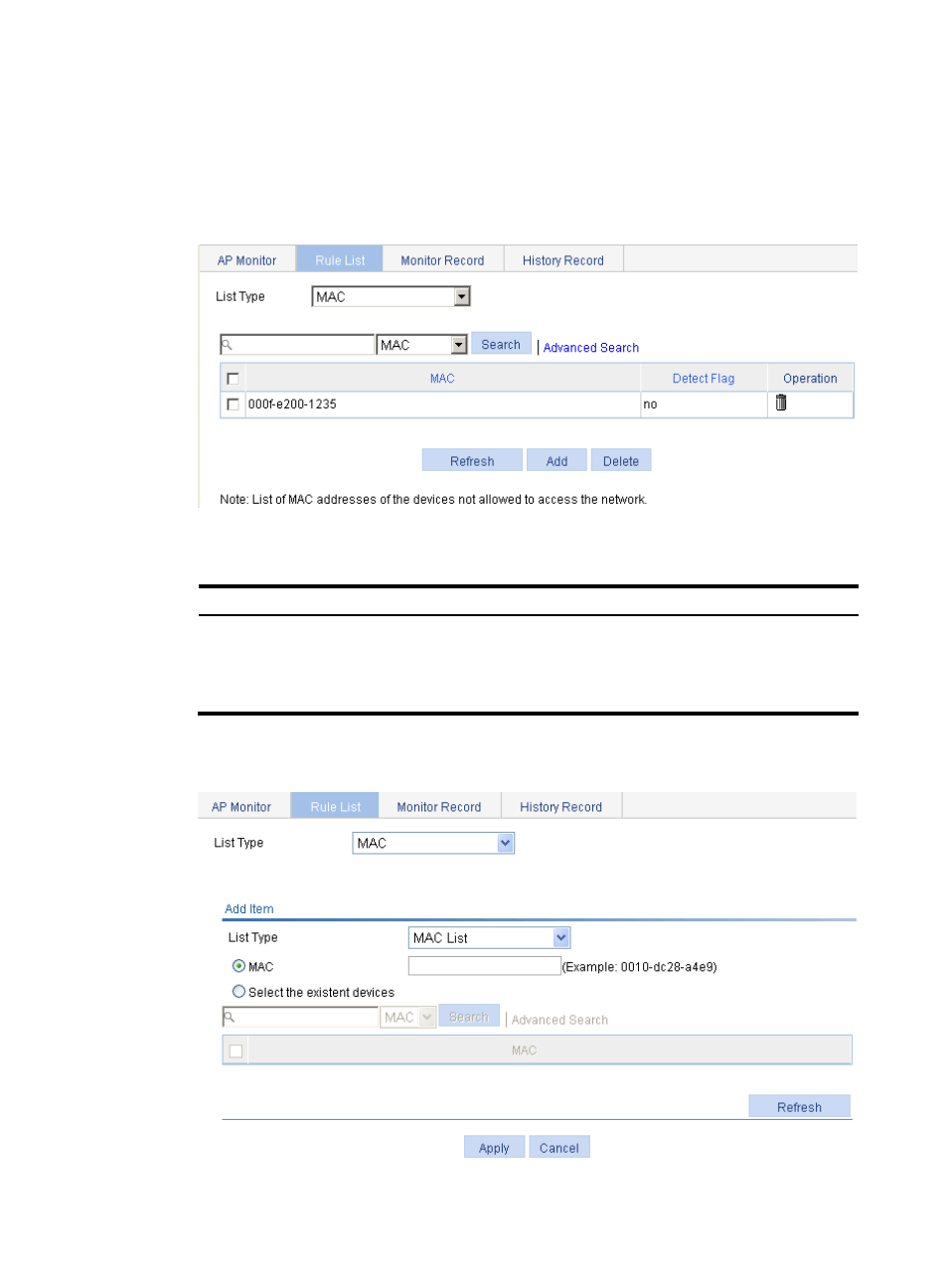
Configuring detection rule lists
1.
Select Security > Rogue Detection from the navigation tree.
2.
Click the Rule List tab.
Figure 654 Configuring a rule list
3.
Configure the rule list as described in
Table 195 Configuration items
Item Description
List Type
•
MAC—Add MAC addresses to be permitted after selecting this option.
•
Wireless Service—Add SSIDs to be permitted after selecting this option.
•
Vendor—Specify vendors to be permitted after selecting this option.
•
Attacker—Add the MAC address of a device to configure the device as a rogue.
4.
Select MAC from the list and click Add.
Figure 655 Configuring a MAC address list
Advertising
This manual is related to the following products: