Wids attack detection, Flood attack detection, Spoofing attack detection – H3C Technologies H3C WX3000E Series Wireless Switches User Manual
Page 634
613
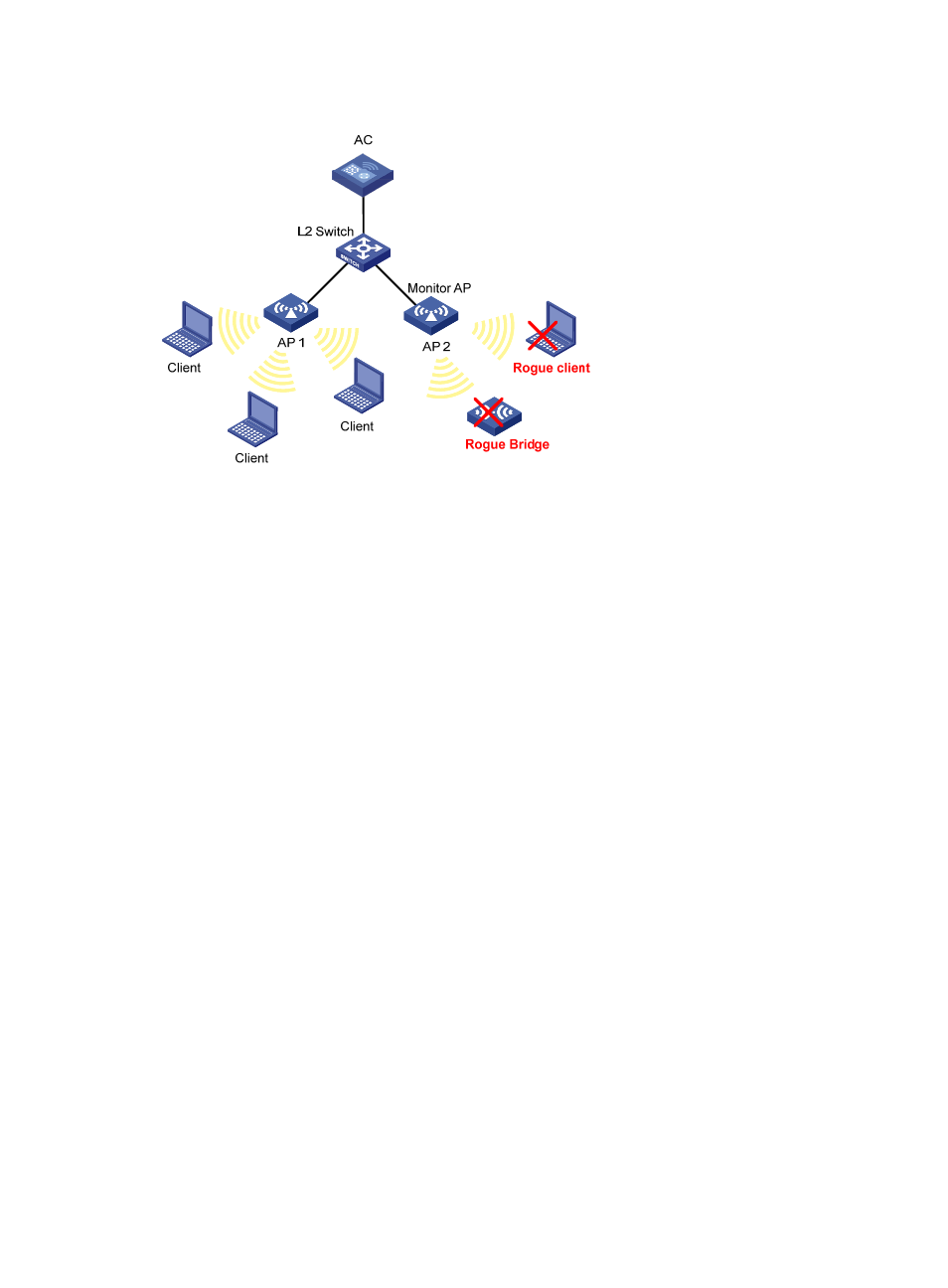
Figure 647 Taking countermeasures against rogue devices
WIDS attack detection
The WIDS attack detection function detects intrusions or attacks on a WLAN network, and informs the
network administrator of the attacks by recording information or sending logs. WIDS detection supports
detection of the following attacks:
•
Flood attack
•
Spoofing attack
•
Weak IV attack
Flood attack detection
A flood attack refers to the case where WLAN devices receive large volumes of frames of the same kind
within a short span of time. When this occurs, the WLAN devices get overwhelmed, and are unable to
service normal clients.
WIDS attacks detection counters flood attacks by constantly keeping track of the density of a specific
kind of packets. When the traffic density of a device exceeds the limit, the device is considered flooding
the network. If the dynamic blacklist feature is enabled, the device is added to the blacklist, and is
forbidden to access the WLAN.
WIDS inspects the following types of frames:
•
Authentication requests and de-authentication requests
•
Association requests, disassociation requests and reassociation requests
•
Probe requests
•
802.11 null data frames
•
802.11 action frames.
Spoofing attack detection
In this kind of attack, a potential attacker can send frames in the air on behalf of another device. For
instance, a client in a WLAN has been associated with an AP and works normally. In this case, a